

Integrated Security
- Build security into the process – technology, facility, personnel
- Enable linkages to allow security in layers and recovery of the losses
- Risk management as a whole not a partial sum of the parts
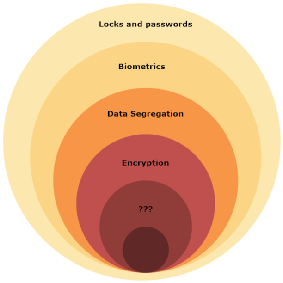
Security – both information and physical security - should be built in layers. That is what we have all heard for years, yet rarely is it explained or achieved. Most companies will have a single layer of security (a lock on the door for example.) Then, with little or no understanding of return on investment, it is determined that the cost of adding more layers is prohibitive. When looking at information security, we often see only a password and user ID as the layer of security. Both of these examples are good starting points, and for some business processes may be all that is required. The key is not only knowing how much security is needed, but also making it an integrated and integral part of the business process.
Where do we start? With an understanding of the business process as well as the legal and regulatory requirements that process has to meet. Then, working as a team, find ways to meet the security challenges without onerous processes and conditions that employees will find ways to circumvent. Yes, that means all security processes and procedures need to take the employees and how they do their jobs into account.
Is there a magic bullet? No. There are many advertisements that would like you to believe that if you do this one thing you are fully protected. Experience shows us that is not the case. Every situation is different and needs to be carefully analyzed and understood in order to make informed and effective decisions. A bit of planning goes a long way into making effective security just another part of our job, not something we have to endure when getting our job done.
Not having a good understanding of your security needs can make itself known in very public ways. Data breaches have almost immediate coverage in the media; a workplace violence situation can quickly harm your reputation and customer base. Protecting your secrets and research and development is just as important; spying and industrial espionage are so prevalent because they work and are a quick way to gain a competitive edge. All of these are things that can keep you from remaining a going concern.
| Fred Bio |
| Keith Bio |
| Business Continuity |
| Technology Risk |
| Integrated Security |
| Operational Effectiveness |
| Memories Preservation |
| Ebola Hype |
| Risk Assessments for Health Care |
| Cyber Threat |
| Data Center Independence |